Today I will show how to install AdGuard Home on PFSense. While I haven’t tested this on OPNSense. The binary for FreeBSD (PFSense) may work on HardendBSD (OPNSense).




Login to your PFSense Firewall web UI and go to Service> DNS Resolver and change the "Listen Port" from port 53 to some other port, I chose 6666. Set Network Interfaces to localhost, there is no need for the pfsense resolver to listen on LAN interface.
To enable rDNS lookups and hostname lookups for devices on your LAN, enable " DHCP Registration" and " Static DHCP" in DNS Resolver settings.

Go to Releases · AdguardTeam/AdGuardHome
Then get the latest version of AdGuard for FreeBSD (as PFSense runs on FreeBSD). Most likely you will have 64Bit version of PFSense so you need AdGuardHome_freebsd_amd64.tar.gz . However if you have 32 Bit PFSense you need AdGuardHome_freebsd_386.tar.gz.
SSH into your PFSense box using Putty or SSH on WSL and enter the following commands:
Make sure to change the url in fetch to the one you got on Step 2 to get latest version.
This command executes AdGuardHome so that we can do initial configuration in the browser.

Go to your router URL with port 3000 on your browser. In my case its http://192.168.5.1:3000 . Replace 192.168.5.1 to your PFSense Address.
It should open the web interface of AdGuard Home.
Click on Get Started.
Now you will see a screen asking to setup interfaces for AdGuard UI and Resolver to run on. You need to set both the Admin Interface and DNS Server Interface to your LAN Interface. In my case it is igb3. It will also show the IP of the Interface next to it to help you identify easily. In my case it is 192.168.5.1 which is the IP Address of my router.

Set the same interface for DNS Server.
Also, make sure to change the Port of web interface from 80 to something that is unlikely to be used on the network. Lets say port 12838. Choose any high port that isn’t likely to conflict with your other applications.
Next enter a username and password for your AdGuard Home. Make sure to use a strong password.
Click on Next and then Open Dashboard.
Now that initial configuration of AdGuard is done. Go back to PFSense SSH and terminate AdGuard using Ctrl+C.
Run this command on the PFSense SSH
Next you will need to install screen so that you can run AdGuard even when ssh is closed.
Lets also install nano text editor so we can write and edit simple text files.
Install shellcmd PFSense Package from WebUI. Its under System>Package Manager>Installed Packages:

Command: /usr/local/bin/screen -S AdGuardHome_screen -d -m /opt/AdGuardHome/AdGuardHome
Shellcmd Type: shellcmd
Description: AdGuard

Click Save
Reboot PFSense and AdGuardHome will start up.
Go to the Web UI of AdGuard Home. It is at http://192.168.5.1:12838 . Where 192.168.5.1 is the IP of your PFSense and 12838 is the Port of Web Interface of AdGuard which we set in Step 4.
Login with your username and password which you set in Step 4.
Now go to Settings>DNS Settings
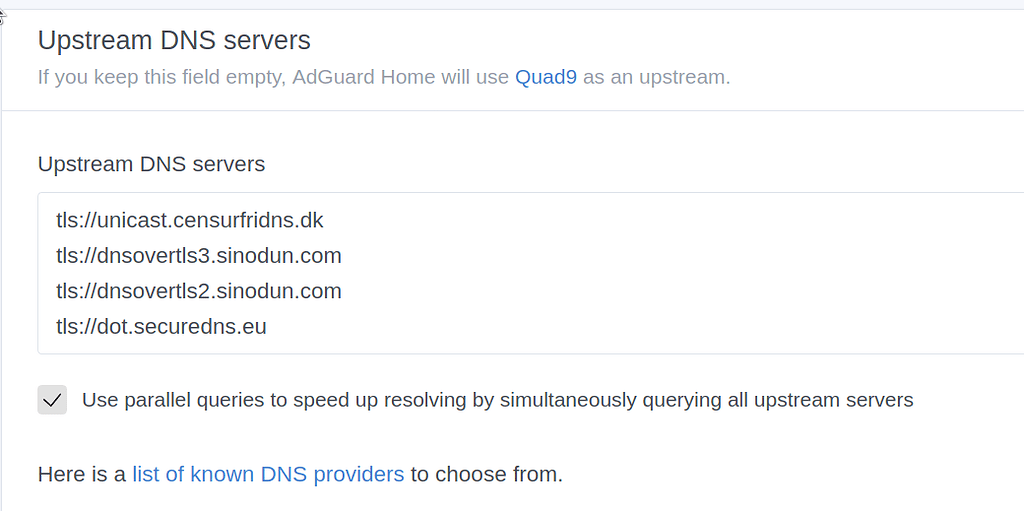
Use the upstream DNS Server of your choice. These are my resolvers

Find more Encrypted DNS Resolvers at DNS Privacy Public Resolvers - DNS Privacy Project - Global Site
Set the query mode to “Parralel Requests” for faster queries.
By default AdGuard Home only uses “AdGuard DNS filter” however you can add your own filters such as
https://www.malwaredomainlist.com/hostslist/hosts.txt
https://raw.githubusercontent.com/StevenBlack/hosts/master/hosts
and enable the filters Disabled by default.
However, keep in mind, higher the number of domains higher the likelihood of false positives.
Go to System> General Setup in PFSense Web Interface and set the DNS Server to 192.168.5.1 and remove any other resolvers.

That’s it AdGuard Home is up and running on PFSense
Go to your PFSense SSH and type in:
Where 192.168.5.1 is the IP of your router
It should output the IP Address of Google.
On Windows you can do
to test the resolver
Why use AdGuard Home?

- Pretty UI: While PFBlockerNG can do DNS Blocking, it has a much more complex UI.
- AdGuard Home UI is easier to use
- Built in Encrypted DNS: AdGuard Home supports build in encrypted DNS (DNS over TLS, DNS over HTTPS).
- Different methods of querying: AdGuard Home supports Parallel Querying where multiple servers are queried at once. This is especially good if you have a unreliable network.
- FreeBSD Support: AdGuard Home supports FreeBSD so you won’t have to virtualize anything.
- Modify DNS TTL to keep DNS Records in cache for longer.

Step 1: Change the Port of your PFSense DNS Resolver


Login to your PFSense Firewall web UI and go to Service> DNS Resolver and change the "Listen Port" from port 53 to some other port, I chose 6666. Set Network Interfaces to localhost, there is no need for the pfsense resolver to listen on LAN interface.
To enable rDNS lookups and hostname lookups for devices on your LAN, enable " DHCP Registration" and " Static DHCP" in DNS Resolver settings.
Step 2: Go to AdGuard home releases page and get the FreeBSD Version:

Go to Releases · AdguardTeam/AdGuardHome
Then get the latest version of AdGuard for FreeBSD (as PFSense runs on FreeBSD). Most likely you will have 64Bit version of PFSense so you need AdGuardHome_freebsd_amd64.tar.gz . However if you have 32 Bit PFSense you need AdGuardHome_freebsd_386.tar.gz.
Step 3: SSH into your PFSense box
Right click and copy the link of the release.SSH into your PFSense box using Putty or SSH on WSL and enter the following commands:
Code:
cd /
mkdir opt
cd opt
fetch https://github.com/AdguardTeam/AdGuardHome/releases/download/v0.104.0-beta2/AdGuardHome_freebsd_amd64.tar.gzMake sure to change the url in fetch to the one you got on Step 2 to get latest version.
Code:
tar -xvf AdGuardHome_freebsd_amd64.tar.gz
cd AdGuardHome
./AdGuardHomeThis command executes AdGuardHome so that we can do initial configuration in the browser.
Step 4: Initial Configuration

Go to your router URL with port 3000 on your browser. In my case its http://192.168.5.1:3000 . Replace 192.168.5.1 to your PFSense Address.
It should open the web interface of AdGuard Home.
Click on Get Started.
Now you will see a screen asking to setup interfaces for AdGuard UI and Resolver to run on. You need to set both the Admin Interface and DNS Server Interface to your LAN Interface. In my case it is igb3. It will also show the IP of the Interface next to it to help you identify easily. In my case it is 192.168.5.1 which is the IP Address of my router.

Set the same interface for DNS Server.
Also, make sure to change the Port of web interface from 80 to something that is unlikely to be used on the network. Lets say port 12838. Choose any high port that isn’t likely to conflict with your other applications.
Next enter a username and password for your AdGuard Home. Make sure to use a strong password.
Click on Next and then Open Dashboard.
Now that initial configuration of AdGuard is done. Go back to PFSense SSH and terminate AdGuard using Ctrl+C.
Step 5: Installing some extra packages:
To make sure that AdGuard gets filters without errors, you will need to install ca_root_nssRun this command on the PFSense SSH
Code:
pkg install ca_root_nssNext you will need to install screen so that you can run AdGuard even when ssh is closed.
Code:
pkg install screenLets also install nano text editor so we can write and edit simple text files.
Code:
pkg install nanoInstall shellcmd PFSense Package from WebUI. Its under System>Package Manager>Installed Packages:

Step 6: Making AdGuard Home start on boot:
Go to Services>shellcmd and click AddCommand: /usr/local/bin/screen -S AdGuardHome_screen -d -m /opt/AdGuardHome/AdGuardHome
Shellcmd Type: shellcmd
Description: AdGuard

Click Save
Reboot PFSense and AdGuardHome will start up.
Step 7: Set Filters and DNS Resolvers for AdGuard Home:
Go to the Web UI of AdGuard Home. It is at http://192.168.5.1:12838 . Where 192.168.5.1 is the IP of your PFSense and 12838 is the Port of Web Interface of AdGuard which we set in Step 4.
Login with your username and password which you set in Step 4.
Now go to Settings>DNS Settings
Use the upstream DNS Server of your choice. These are my resolvers
Code:
https://dns10.quad9.net/dns-query
tls://dns.google
tls://1.1.1.1
https://doh.opendns.com/dns-query
Find more Encrypted DNS Resolvers at DNS Privacy Public Resolvers - DNS Privacy Project - Global Site
Set the query mode to “Parralel Requests” for faster queries.
By default AdGuard Home only uses “AdGuard DNS filter” however you can add your own filters such as
https://www.malwaredomainlist.com/hostslist/hosts.txt
https://raw.githubusercontent.com/StevenBlack/hosts/master/hosts
and enable the filters Disabled by default.
However, keep in mind, higher the number of domains higher the likelihood of false positives.
Step 8: Set PFSense to use the AdGuard DNS:
Go to System> General Setup in PFSense Web Interface and set the DNS Server to 192.168.5.1 and remove any other resolvers.

That’s it AdGuard Home is up and running on PFSense
Step 9: Test AdGuard
Go to your PFSense SSH and type in:
Code:
dig @192.168.5.1 google.comWhere 192.168.5.1 is the IP of your router
It should output the IP Address of Google.
dig @192.168.5.1 google.com
; <<>> DiG 9.16.1-Ubuntu <<>> @192.168.5.1 google.com
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 946
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 0
;; QUESTION SECTION:
;google.com. IN A
;; ANSWER SECTION:
google.com. 10 IN A 74.125.130.147
;; Query time: 0 msec
;; SERVER: 192.168.5.1#53(192.168.5.1)
;; WHEN: Thu Jan 07 16:34:08 IST 2021
;; MSG SIZE rcvd: 44
On Windows you can do
Code:
nslookup google.com 192.168.5.1to test the resolver
Last edited: